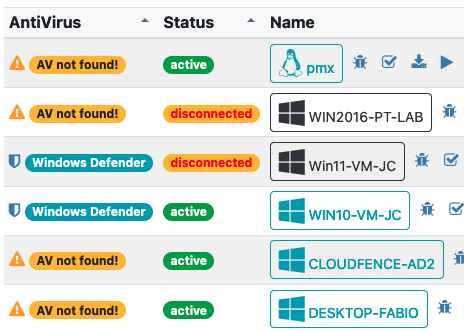
Specialized protection for small and medium-sized businesses
With support for Windows, Linux and Mac OS systems, our EDR Cloudfence has been meticulously developed to provide proactive action in the identification and continuous monitoring of your network endpoints. This solution, managed and closely monitored by our Security Operations Center (SOC), ensures a supreme level of readiness and security.
Real-time monitoring
Keep up to date with the latest incidents, vulnerabilities and alerts under the watchful eye of our SOC, receiving instant updates to ensure the continued security of your environment.
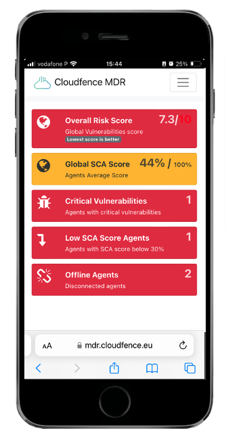
Managed Antivirus
Through direct integration with Windows Defender, we offer the ability to efficiently manage all access points with this antivirus. Don't worry if you prefer to continue with your current antivirus solution, our EDR system is designed to be compatible with the vast majority of antiviruses available on the market.

Score for Secure Configurations
Protect your endpoints from configurations exposed to vulnerabilities and risks by receiving a detailed score accompanied by recommendations for corrections in line with the most effective industry practices.
Identifying Threats and Malicious Processes
We identify and eliminate hidden cyber threats with our threat hunting solution. We analyze logs, network traffic and endpoint data to protect your IT environment, ensuring security beyond traditional measures.

Identifying and neutralizing attacks in a matter of minutes
With native integration with our SOC, EDR effectively detects threats such as brute force attacks against passwords, exploits of vulnerabilities, installation of malicious software, and other anomalies. This detection ability allows our SOC, together with the customer, to take quick and effective action to neutralize these threats.
